D Link Update Firmware On Router
Content/Images/uploaded/gamal%20choukri/New%20Folder%20(4)/DIR-600L_Datasheet_US-1.jpg' alt='D Link Update Firmware On Router' title='D Link Update Firmware On Router' />Security for your DLink router Various media reports have recently been published relating to vulnerabilities in network routers, including DLink devices. DLink helps you connect to more of everything. We offer awardwinning networking products and services for home consumers, businesses, and service providers. Get support for Linksys WirelessN Gigabit Router. Based on the above strings listing, the binwebs binary is a modified version of thttpd which provides the administrative interface for the router. Researcher discloses 1. D Link zero day router flaws. D Link. When a zero day vulnerability becomes public, of which by its nature no patches or fixes are available at the time, one is enough for vendors to come to terms with in order to rapidly devise a solution. D Link now has 1. Last week, security researcher Pierre Kim chose to publicly disclose his findings related to D Link 8. L routers due to difficulties working with the vendor on a coordinated disclosure. In a blog post, Kim said the flaws were found in the D Link 8. L, a wireless AC1. Mydlink Cloud Services to access their home networks remotely. Kim describes the product as a router overall badly designed with a lot of vulnerabilities, and says that he was able to compromise everything, from the LAN to the WAN, as well as the custom My. D Link Update Firmware On Router' title='D Link Update Firmware On Router' />Email Settings. The Email feature can be used to send the system log files, router alert messages, and firmware update notification to your email address. Manual Revision A Firmware Manual Revision B Firmware. If youve got a DLink DIR850L AC1200 router, its time to think about replacing it the holes in the firmware might never be fixed. Researcher discloses 10 DLink zeroday router flaws. The security researcher says the general public should immediately disconnect their router until patches are. Le6JvUU8Zs/UnNt4TWsrjI/AAAAAAAAC8I/nWrI2WNbYBA/s1600/2.PNG]];var lpix_1=pix_1.length;var p1_0= [[611' alt='D Link Update Firmware On Router' title='D Link Update Firmware On Router' />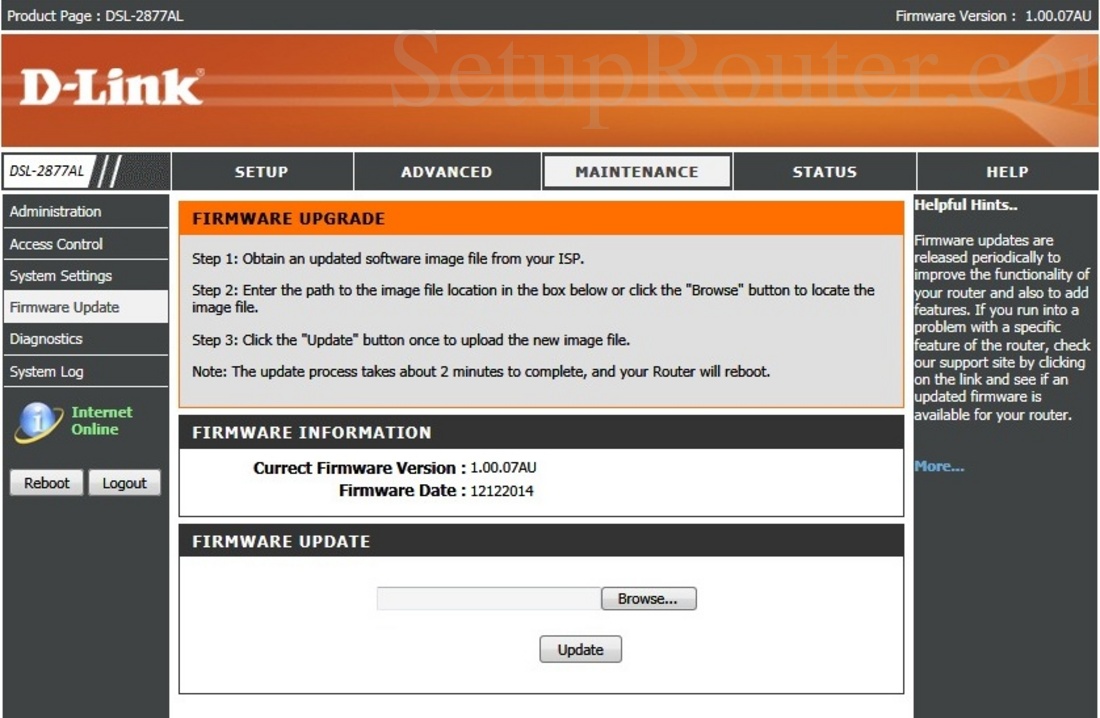 Dlink cloud protocol. There are two different versions of the router, rev. A and rev. B, available and the vulnerabilities below impact both. Firmware protection The latest firmware for version A is not protected and firmware images can be forged by attackers. Version B firmware is password protected with a hardcoded password in other words, extremely poorly. WAN LAN rev. A XSS PHP files found within the router system can be exploited and if attackers use a number of XSS flaws within, they can steal authentication cookies. WAN LAN rev. B Retrieving admin password, gaining full access using the custom mydlink Cloud protocol Without breaking D Links terms of use, Kim found vulnerabilities which could allow attackers to abuse the My. DLink cloud protocol and register the router to their own accounts to gain full, unfettered access. WAN rev. A and rev. B Weak Cloud protocol The My. Dlink Cloud protocol is little more than a basic TCP relay system and has no encryption by default. Traffic is sent over TCP to Amazon servers without encryption. To make matters worse, the router interface allows users to enter credentials for their email accounts, which are then sent from the router to server without encryption or suitable verification. Passwords are also stored in cleartext. LAN rev. B Backdoor access The router model has a backdoor which can be accessed by logging in with Alphanetworks and a supplied password, granting an attacker root access and control. WAN LAN rev. A and rev. B Stunnel private keys The routers stunnel private keys are hardcoded, which paves the way for SSL Man in The Middle Mi. TM attacks. WAN LAN rev. A Nonce bruteforcing for DNS configuration DNS configuration can be changed without admin user authentication checks, allowing for routing and bruteforce attacks. Local rev. A and rev. B Weak files permission and credentials stored in cleartext Some files have weak permission setups and store credentials in cleartext. WAN rev. B Pre Auth RCEs as root L2 The DCHP client running on the router is vulnerable to a number of command injections as root, leading to potential remote code execution. If a vulnerable router is connected to an internal network, the attack will also make the network vulnerable to exploit. LAN rev. A and rev. B Do. S against some daemons A number of daemons can be crashed remotely. The bugs were discovered in June this year, the advisory was written up in July, and the public advisory appearing on security mailing lists last week. Due to difficulties in previous exchanges with D Link, Full disclosure is applied, Kim says. Their previous lack of consideration about security made me publish this research without coordinated disclosure. Frozen Throne Free Download Installer more. I advise to immediately disconnect vulnerable routers from the Internet, the researcher added. According to the security researcher, he has chosen full disclosure even though no patches have been issued to fix all of the issues. Kim has apparently experienced trouble with D Link in the past, with a disclosure last February resulting in no acknowledgment from the vendor, but rather just the silent issue of a patch which fixed only one problem of many. Rather than contact the researcher, D Link apparently downplayed the findings, claiming the security researcher found the issues by chance. ZDNet has reached out to D Link and will update if we hear back. Previous and related coverage. Router flaws put AT T customers at hacking risk. The bugs are easy to exploit, but can be easily mitigated. CIA has been hacking into Wi Fi routers for years, leaked documents show. The hacking tools target hundreds of models developed by dozens of router manufacturers. Virgin Media tells 8. Ethical hackers carried out research on the Super Hub 2 router and found it could be used to take control of Internet of Things devices. Another Day, Three More D Link Router Vulnerabilities. Its been a bad year to own a D Link router. A few days after a Korean researcher revealed 1. D Link router model, a separate security firm has unearthed three more flaws in three more models, and even provided proof of concept exploits. D Links DIR 8. L router. Credit D Link. The similarities run even deeper, as both entities contacted D Link before going public, but decided that the company was not able to fix router flaws on a user friendly timescale. D Link has already patched one of the newfound flaws, but the other two are still very much a risk, and the only surefire way to protect yourself is to use a different router. The new report comes from Embedi, a Berkeley, California based security firm that focuses on hardware protection. Researchers at the company discovered three exploitable flaws in D Links DIR 8. L, DIR 8. 85. L and DIR 8. L routers, but believe that other models in the DIR 8. XX line are probably also cruising for a bruising. The separate flaw we wrote about yesterday involved the DIR 8. L model. MORE Best Wi Fi Routers. First things first Updating your D Link router to the latest firmware will solve one problem that Embedi found. If youre not sure how to do this, visit the D Link tech support site and search for your router model. Embedi discovered a flaw in the routers phpcgi protocol, which in extremely simple terms processes authorization requests for the router. By sending a cleverly programmed but inauthentic request, researchers were able to suss out a routers username and password. However, even though Embedi notified D Link about the routers other problems three months ago, two of the flaws remain unpatched. One of them involves a stack overflow error, which basically just floods the system with nonsense data until it does what the attackers want it to do. The other flaw ironically lets an attacker hijack a router by trying to update firmware in a routers recovery mode. So maybe its not worth updating your firmware just yet. Since a router controls an entire home networks internet traffic, it doesnt take much imagination to expostulate what a hacker could do with these flaws. Intercepting internet traffic including logins for email, social media and financial institutions would be simple, as would redirecting queries for popular websites to malicious pages that could steal credentials or inject malware. Embedi may not have helped matters, as it posted working exploits for each flaw on its Github page. Toms Guide has contacted D Link for comment on the story, but has not yet received a response. For now, if you use a D Link router but have a spare stashed away somewhere, its probably better to use your backup. Netgear and Linksys routers arent perfect, but they at least have a pretty good track record of patching their flaws in a timely manner.
Dlink cloud protocol. There are two different versions of the router, rev. A and rev. B, available and the vulnerabilities below impact both. Firmware protection The latest firmware for version A is not protected and firmware images can be forged by attackers. Version B firmware is password protected with a hardcoded password in other words, extremely poorly. WAN LAN rev. A XSS PHP files found within the router system can be exploited and if attackers use a number of XSS flaws within, they can steal authentication cookies. WAN LAN rev. B Retrieving admin password, gaining full access using the custom mydlink Cloud protocol Without breaking D Links terms of use, Kim found vulnerabilities which could allow attackers to abuse the My. DLink cloud protocol and register the router to their own accounts to gain full, unfettered access. WAN rev. A and rev. B Weak Cloud protocol The My. Dlink Cloud protocol is little more than a basic TCP relay system and has no encryption by default. Traffic is sent over TCP to Amazon servers without encryption. To make matters worse, the router interface allows users to enter credentials for their email accounts, which are then sent from the router to server without encryption or suitable verification. Passwords are also stored in cleartext. LAN rev. B Backdoor access The router model has a backdoor which can be accessed by logging in with Alphanetworks and a supplied password, granting an attacker root access and control. WAN LAN rev. A and rev. B Stunnel private keys The routers stunnel private keys are hardcoded, which paves the way for SSL Man in The Middle Mi. TM attacks. WAN LAN rev. A Nonce bruteforcing for DNS configuration DNS configuration can be changed without admin user authentication checks, allowing for routing and bruteforce attacks. Local rev. A and rev. B Weak files permission and credentials stored in cleartext Some files have weak permission setups and store credentials in cleartext. WAN rev. B Pre Auth RCEs as root L2 The DCHP client running on the router is vulnerable to a number of command injections as root, leading to potential remote code execution. If a vulnerable router is connected to an internal network, the attack will also make the network vulnerable to exploit. LAN rev. A and rev. B Do. S against some daemons A number of daemons can be crashed remotely. The bugs were discovered in June this year, the advisory was written up in July, and the public advisory appearing on security mailing lists last week. Due to difficulties in previous exchanges with D Link, Full disclosure is applied, Kim says. Their previous lack of consideration about security made me publish this research without coordinated disclosure. Frozen Throne Free Download Installer more. I advise to immediately disconnect vulnerable routers from the Internet, the researcher added. According to the security researcher, he has chosen full disclosure even though no patches have been issued to fix all of the issues. Kim has apparently experienced trouble with D Link in the past, with a disclosure last February resulting in no acknowledgment from the vendor, but rather just the silent issue of a patch which fixed only one problem of many. Rather than contact the researcher, D Link apparently downplayed the findings, claiming the security researcher found the issues by chance. ZDNet has reached out to D Link and will update if we hear back. Previous and related coverage. Router flaws put AT T customers at hacking risk. The bugs are easy to exploit, but can be easily mitigated. CIA has been hacking into Wi Fi routers for years, leaked documents show. The hacking tools target hundreds of models developed by dozens of router manufacturers. Virgin Media tells 8. Ethical hackers carried out research on the Super Hub 2 router and found it could be used to take control of Internet of Things devices. Another Day, Three More D Link Router Vulnerabilities. Its been a bad year to own a D Link router. A few days after a Korean researcher revealed 1. D Link router model, a separate security firm has unearthed three more flaws in three more models, and even provided proof of concept exploits. D Links DIR 8. L router. Credit D Link. The similarities run even deeper, as both entities contacted D Link before going public, but decided that the company was not able to fix router flaws on a user friendly timescale. D Link has already patched one of the newfound flaws, but the other two are still very much a risk, and the only surefire way to protect yourself is to use a different router. The new report comes from Embedi, a Berkeley, California based security firm that focuses on hardware protection. Researchers at the company discovered three exploitable flaws in D Links DIR 8. L, DIR 8. 85. L and DIR 8. L routers, but believe that other models in the DIR 8. XX line are probably also cruising for a bruising. The separate flaw we wrote about yesterday involved the DIR 8. L model. MORE Best Wi Fi Routers. First things first Updating your D Link router to the latest firmware will solve one problem that Embedi found. If youre not sure how to do this, visit the D Link tech support site and search for your router model. Embedi discovered a flaw in the routers phpcgi protocol, which in extremely simple terms processes authorization requests for the router. By sending a cleverly programmed but inauthentic request, researchers were able to suss out a routers username and password. However, even though Embedi notified D Link about the routers other problems three months ago, two of the flaws remain unpatched. One of them involves a stack overflow error, which basically just floods the system with nonsense data until it does what the attackers want it to do. The other flaw ironically lets an attacker hijack a router by trying to update firmware in a routers recovery mode. So maybe its not worth updating your firmware just yet. Since a router controls an entire home networks internet traffic, it doesnt take much imagination to expostulate what a hacker could do with these flaws. Intercepting internet traffic including logins for email, social media and financial institutions would be simple, as would redirecting queries for popular websites to malicious pages that could steal credentials or inject malware. Embedi may not have helped matters, as it posted working exploits for each flaw on its Github page. Toms Guide has contacted D Link for comment on the story, but has not yet received a response. For now, if you use a D Link router but have a spare stashed away somewhere, its probably better to use your backup. Netgear and Linksys routers arent perfect, but they at least have a pretty good track record of patching their flaws in a timely manner.