The 2. 14 traditional kanji radicals and their meanings. Kanji are classified in kanji dictionaries according to their main components which are called radicals roots in English and in Japanese. There are 2. 14 historical radicals derived from the 1. Kangxi dictionary. Every kanji without exception only has one radical. Each radical has a meanings and lends its meanings to the kanji of which it is part. Please take a look at the examples below. The right part of these three kanji is the same but the left part is different. The left part of these kanji is their radical. Note how each radical imparts its meaning to the kanji The radical of this kanji is sun, day, time. The meaning of this kanji is time. The radical of this kanji is words, to speak, say. The meaning of this kanji is poetry, poem. The radical of this kanji is hand. Download free Japanese unicode, handwriting, calligraphy fonts and more that can be used in commercial works Teachers and students can use these comprehensive Japanese language guides to improve reading, writing, and comprehension skills for beginner, intermediate and. t. The meaning of this kanji is to hold. For this reason it is very important to learn each kanjis radical, as well as the meanings of its radical. Not all 2. 14 radicals are in use in current Japanese but you will soon become familiar with the most important ones and their variants. There are no official Japanese names for radicals. But there are certain commonly used names. That is why you will find differences in the Japanese names for the radicals on different websites and dictionaries. Radicals are categorized into seven main groups according to their position within a kanji. Please note that some kanji are also radicals in and of themselves such as, ,. In those cases, the kanji and the radical are one and the same, and thus the position of the radical in the kanji is irrelevant. As a result they do not fall into any one of the seven categories. With our web application http app. Advanced Search syntax for example, rjn miru or rjn to search by Japanese name, rs 7 to search by stroke number, rem see to search by English meaning, and rpos or rpos tsukuri to search for kanji by the position of the radical. Please consult our User Guide to learn about additional search options. Tip By default, the radicals in the list below are presented in ascending stroke order. However you can also focus on a specific stroke number or look for individual radicals by using the Search field at the top of the table. Alternatively you can click on a column heading to sort the entire table by that heading. This is also a good way to focus on just the most important radicals. Clicking on the a variant of. link scrolls the page to the original version of that radical. Tip You can also use the tables own search field to searchfilter radicals by position. Use the radical positions table as a reference. For example, to view all radicals in the hang down position, type or tare into the search field. To avoid ambiguities amongst the different kinds of enclosed radicals, search for these in hiragana. Placing your mouse pointer over any position symbol in the radical table reveals its Japanese name. Fonts Many of the radical characters shown on this list are not supported by the Japanese fonts widely used on Windows, OS X or Linux some not even in Unicode. For these reasons we created Japanese Radicals, an open source font derived from Source Han Sans with 6. Japanese radical and variant. The font is freely available for private or commercial use. Tip If youd like a copy of the radicals tables in a format better suited for printing or if youd like to re use this data in another application, please visit our open source repository on Git.  Kanji Font EnglishHub. Most of the language data and media files used in Kanji alive are freely available under a Creative Commons CC BY license. StrokeRadical. Position. Meaning. Reading. Notes. Importance. Important. 2person2persona variant of Important. Important. 2human legsImportant.
Kanji Font EnglishHub. Most of the language data and media files used in Kanji alive are freely available under a Creative Commons CC BY license. StrokeRadical. Position. Meaning. Reading. Notes. Importance. Important. 2person2persona variant of Important. Important. 2human legsImportant.  Important. 2ice2table2winda variant of 2container, open box2knife, sword2knife, sworda variant of Important. Important. 2private, Katakana Mu2again, right hand3mouth3moutha variant of Important. Important. 3earth3eartha variant of Important. Important. 3child, son3child, sona variant of Important. Important. 3inch, 2. Important. 3to move, stretch3folded hands3javelin3bow in archery3bow in archerya variant of 3pigs head3pigs heada variant of 3pigs heada variant of 3hair style, light rays3step, stride, street, to goImportant. Important. 3road, walk, to advancea variant of Important. Important. 3hill, mounda variant of Important. Katakana Tsu3heart, mind, spirita variant of Important. Important. 3watera variant of Important. Important. 4heart, mind, spirit4heart, mind, spirita variant of 4spear, weapon4door4doora variant of 4hand4branch4activity, to strike, hit4activity, to strike, hita variant of Important. Important. 4to say4moon, month, period4moon, month, perioda variant of 4meat, flesha variant of Important. Important. 4to lack, yawn4to stop4death dying, to decompose4death dying, to decomposea variant of 4lance shaft, action4not, mother4to compare4hair4family, clan4steam, air4water4fire4firea variant of Important. Important. 4claw, nail4claw, naila variant of 4claw, naila variant of 4father4to mix4split wood4split wood4split wooda variant of 4fang, canine tooth4cow4cowa variant of 4dog4jewelry, jeweled kinga variant of Important.
Important. 2ice2table2winda variant of 2container, open box2knife, sword2knife, sworda variant of Important. Important. 2private, Katakana Mu2again, right hand3mouth3moutha variant of Important. Important. 3earth3eartha variant of Important. Important. 3child, son3child, sona variant of Important. Important. 3inch, 2. Important. 3to move, stretch3folded hands3javelin3bow in archery3bow in archerya variant of 3pigs head3pigs heada variant of 3pigs heada variant of 3hair style, light rays3step, stride, street, to goImportant. Important. 3road, walk, to advancea variant of Important. Important. 3hill, mounda variant of Important. Katakana Tsu3heart, mind, spirita variant of Important. Important. 3watera variant of Important. Important. 4heart, mind, spirit4heart, mind, spirita variant of 4spear, weapon4door4doora variant of 4hand4branch4activity, to strike, hit4activity, to strike, hita variant of Important. Important. 4to say4moon, month, period4moon, month, perioda variant of 4meat, flesha variant of Important. Important. 4to lack, yawn4to stop4death dying, to decompose4death dying, to decomposea variant of 4lance shaft, action4not, mother4to compare4hair4family, clan4steam, air4water4fire4firea variant of Important. Important. 4claw, nail4claw, naila variant of 4claw, naila variant of 4father4to mix4split wood4split wood4split wooda variant of 4fang, canine tooth4cow4cowa variant of 4dog4jewelry, jeweled kinga variant of Important. 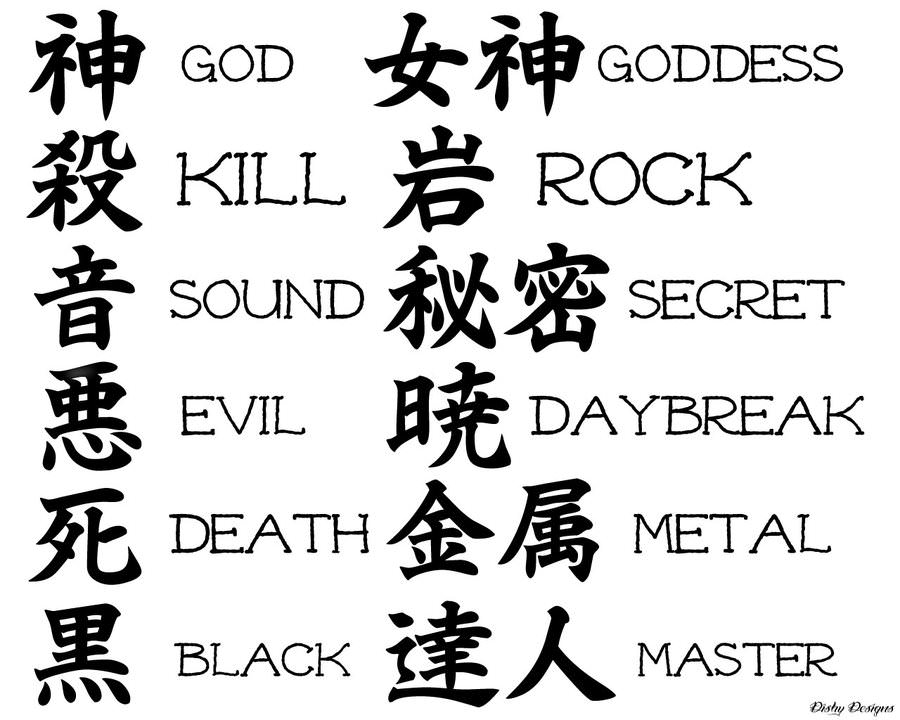 Shodo Japanese calligraphy Youve seen people with tattoos of kanji symbols. Youve seen bookmarks and mood stones. The beauty and simplicity of Shodo Japanese. Important. 4neta variant of 4old, old agea variant of 5darkness5jewelry5melon5tile5sweet5birth, to be born, live5to use5rice paddy5rice paddya variant of 5bolt of cloth5bolt of clotha variant of 5sicknessImportant. Important. 5eyea variant of 5halberd5halberda variant of 5arrow5arrowa variant of 5stone5stonea variant of 5altar, festival, religious service5footprint5grainImportant. Important. 5to stand5to standa variant of 5fang, canine tootha variant of 5fang, canine tootha variant of 5watera variant of 5neta variant of 5neta variant of 5clothinga variant of Important. Important. 6rice6ricea variant of Important. Important. 6earthen jar6net6sheep6sheepa variant of 6feather, wing6feather, winga variant of 6old, old age6and also6plow6ear6eara variant of 6writing brush6flesh, meat6retainer, minister6self6to arrive, reach6to arrive, reacha variant of 6mortar, quern6tongue6contrary, to err6ship, boat6ship, boata variant of 6boundary6color6grass, plant6tiger6worm, insect, bug6worm, insect, buga variant of Important. Important. 6clothing6cover, west6cover, westa variant of 6melona variant of 7to see7horn, corner7horn, cornera variant of 7words, to speak, say7words, to speak, saya variant of Important. Important. 7red7to run7to runa variant of Important. Kanji Wikipdia. Les kanjis1 sont des caractres chinois dont la fonction est dcrire une partie de la langue japonaise en associant chaque signe une matrice de sens signifis et de lectures valeurs phonologiques. Le mot kanji vient du japonais romaniskanji, qui est la transcription du terme un mot compos prcisment de deux kanjis. Il sagit de caractres, ji utiles lcriture du japonais, qui ont t emprunts pour la plupart au systme dcriture de lethnie chinoise han, kan littralement donc des caractres chinois ou sinogrammes 2. Les kanjis forment lun des grands ensembles de caractres mojishu de lcriture au Japon, avec dune part les kanas, syllabaires3 spcifiquement japonais composs des hiraganas et katakanas, et, dautre part, les emprunts au monde occidental, savoir les lettres latines rmaji et les chiffres arabes. Lorigine des kanjis est, par dfinition, celle de lcriture dveloppe dans la Chine antique laquelle dbute, si on se limite aux plus anciens documents connus, avec lcriture osscaille la fin de la dynastie Shang. Quant lpoque de limportation des sinogrammes au Japon, celle ci nest pas connue avec exactitude le Kojiki 7. Archipel. Par ailleurs, la tradition considre que lon doit lenseignement des caractres chinois auprs de la cour impriale japonaise au lettr Wani, venu du royaume de Baekje5. La caractristique la plus remarquable des kanjis, comme des sinogrammes en gnral, est le lien quil existe entre chaque signe et un ensemble de sens jigi, lien qui dcoule de la nature logographique des sinogrammes, chacun de ces derniers codant gnralement un mot ou un morphme de la langue chinoise antique. Cela les oppose, par exemple, aux lettres latines ou aux kanas, qui ne reprsentent intrinsquement que des sons. Dans le modle de lcriture japonaise mlant kanjis et kanas kanji kana majiribun6, les kanjis sont gnralement utiliss pour crire la racine des mots, lhabillage grammatical de la phrase tant crit en syllabaires7 hiraganas. En outre, sur le plan de sa prononciation, cette criture nest pas univoque, car un mme kanji dans la langue crite peut souvent se raliser de diffrentes manires dans la langue orale on parle de ses diffrentes lectures, en japonais yomi ou onkun8, qui correspondent chacunes une ou plusieurs mores. Le fait que ces caractres sont inclus dans un ensemble dsign sous le terme gnrique de caractres chinois ne doit pas se comprendre comme une simple inclusion des kanjis dans un systme scriptural purement chinois ce qui constitue nanmoins une bonne premire approximation. Kanji Font DownloadEn plus du fait que les lectures des kanjis se distinguent des lectures observes au sein des langues chinoises, il existe un nombre important de spcificits nipponnes quant lapparence graphique voire aux valeurs smantiques des kanjis ces points seront plus amplement dtaills dans la suite de larticle. Dautre part, il est intressant de noter quil existe, de surcroit, une petite proportion de kanjis dits nationaux , kokuji, qui sont ns au Japon.
Shodo Japanese calligraphy Youve seen people with tattoos of kanji symbols. Youve seen bookmarks and mood stones. The beauty and simplicity of Shodo Japanese. Important. 4neta variant of 4old, old agea variant of 5darkness5jewelry5melon5tile5sweet5birth, to be born, live5to use5rice paddy5rice paddya variant of 5bolt of cloth5bolt of clotha variant of 5sicknessImportant. Important. 5eyea variant of 5halberd5halberda variant of 5arrow5arrowa variant of 5stone5stonea variant of 5altar, festival, religious service5footprint5grainImportant. Important. 5to stand5to standa variant of 5fang, canine tootha variant of 5fang, canine tootha variant of 5watera variant of 5neta variant of 5neta variant of 5clothinga variant of Important. Important. 6rice6ricea variant of Important. Important. 6earthen jar6net6sheep6sheepa variant of 6feather, wing6feather, winga variant of 6old, old age6and also6plow6ear6eara variant of 6writing brush6flesh, meat6retainer, minister6self6to arrive, reach6to arrive, reacha variant of 6mortar, quern6tongue6contrary, to err6ship, boat6ship, boata variant of 6boundary6color6grass, plant6tiger6worm, insect, bug6worm, insect, buga variant of Important. Important. 6clothing6cover, west6cover, westa variant of 6melona variant of 7to see7horn, corner7horn, cornera variant of 7words, to speak, say7words, to speak, saya variant of Important. Important. 7red7to run7to runa variant of Important. Kanji Wikipdia. Les kanjis1 sont des caractres chinois dont la fonction est dcrire une partie de la langue japonaise en associant chaque signe une matrice de sens signifis et de lectures valeurs phonologiques. Le mot kanji vient du japonais romaniskanji, qui est la transcription du terme un mot compos prcisment de deux kanjis. Il sagit de caractres, ji utiles lcriture du japonais, qui ont t emprunts pour la plupart au systme dcriture de lethnie chinoise han, kan littralement donc des caractres chinois ou sinogrammes 2. Les kanjis forment lun des grands ensembles de caractres mojishu de lcriture au Japon, avec dune part les kanas, syllabaires3 spcifiquement japonais composs des hiraganas et katakanas, et, dautre part, les emprunts au monde occidental, savoir les lettres latines rmaji et les chiffres arabes. Lorigine des kanjis est, par dfinition, celle de lcriture dveloppe dans la Chine antique laquelle dbute, si on se limite aux plus anciens documents connus, avec lcriture osscaille la fin de la dynastie Shang. Quant lpoque de limportation des sinogrammes au Japon, celle ci nest pas connue avec exactitude le Kojiki 7. Archipel. Par ailleurs, la tradition considre que lon doit lenseignement des caractres chinois auprs de la cour impriale japonaise au lettr Wani, venu du royaume de Baekje5. La caractristique la plus remarquable des kanjis, comme des sinogrammes en gnral, est le lien quil existe entre chaque signe et un ensemble de sens jigi, lien qui dcoule de la nature logographique des sinogrammes, chacun de ces derniers codant gnralement un mot ou un morphme de la langue chinoise antique. Cela les oppose, par exemple, aux lettres latines ou aux kanas, qui ne reprsentent intrinsquement que des sons. Dans le modle de lcriture japonaise mlant kanjis et kanas kanji kana majiribun6, les kanjis sont gnralement utiliss pour crire la racine des mots, lhabillage grammatical de la phrase tant crit en syllabaires7 hiraganas. En outre, sur le plan de sa prononciation, cette criture nest pas univoque, car un mme kanji dans la langue crite peut souvent se raliser de diffrentes manires dans la langue orale on parle de ses diffrentes lectures, en japonais yomi ou onkun8, qui correspondent chacunes une ou plusieurs mores. Le fait que ces caractres sont inclus dans un ensemble dsign sous le terme gnrique de caractres chinois ne doit pas se comprendre comme une simple inclusion des kanjis dans un systme scriptural purement chinois ce qui constitue nanmoins une bonne premire approximation. Kanji Font DownloadEn plus du fait que les lectures des kanjis se distinguent des lectures observes au sein des langues chinoises, il existe un nombre important de spcificits nipponnes quant lapparence graphique voire aux valeurs smantiques des kanjis ces points seront plus amplement dtaills dans la suite de larticle. Dautre part, il est intressant de noter quil existe, de surcroit, une petite proportion de kanjis dits nationaux , kokuji, qui sont ns au Japon.  Par exemple, sakaki, qui dsigne un arbre sacr dans la religion shinto, est un kanji apparu au Japon il provient de la fusion des caractres et, respectivement arbre et divinit 9. Les kanjis tant lorigine des caractres reprsentant des mots ou morphmes chinois, et non japonais, leur introduction pour transcrire la langue japonaise ne conduisit pas une lecture univoque. Les prononciations associes en Chine aux sinogrammes ont donn ce quon appelle les lectures sino japonaises on en japonais onyomi voir le sinogramme le son. Aprs limportation de caractres ou concepts chinois, la langue japonaise a souvent conserv la mmoire de ces prononciations trangres, mmoire qui a nanmoins pu voluer depuis, suivant lvolution phontique du japonais. Quand le concept existait en japonais, il put aussi tre traduit et vocalis suivant les mots de la langue nipponne originelle, la lecture du caractre se faisant donc la japonaise ces lectures sont dites kun en japonais kunyomi voir le sinogramme instruire, exgse. La plupart des kanjis a de ce fait au moins deux lectures possibles on et kun. Ce nest toutefois pas une rgle absolue, et lon trouve des kanjis sans lecture kun comme kiku, chrysanthme, ou sans lecture on comme iwashi, sardine labsence de lecture on est videmment frquente pour les kanjis crs au Japon, les kokuji. Pour les mots composs de deux kanjis ou plus, jukugo, les lectures hybrides abondent. Par exemple, en cuisine, gy niku, buf et y niku, mouton ont une lecture de type on on, mais buta niku, porc et tori niku, volaille ont en revanche des lectures kun on ces dernires lectures sont qualifies de lectures yut, yutyomi. Hormis le cas simple des caractre nayant quune seule lecture, on ou kun selon les cas, la majorit des kanjis rencontrs dans les textes japonais sont pourvus de deux lectures ou davantage. Ainsi, certains kanjis dusage courant peuvent avoir plus dune dizaine de lectures possibles. On trouve par exemple le kanji signifiant notamment la vie ou vivre dont les lectures officielles sont sei, sh, i kasu1. Souvent, donc, dterminer la lecture dun kanji suppose davoir identifi correctement le sens dans lequel il est employ. Il faut pour cela observer un ou plusieurs signes situs son voisinage, voire juger plus largement en fonction du contexte. Par exemple, lhomographe peut soit faire rfrence au mot kaze vent soit au mot f apparence, style il est donc ncessaire de deviner en amont, par le contexte, la valeur smantique de pour pouvoir le lire. Dautre part, dans les mots composs contenant, cette nette distinction disparait, la lecture f pouvant parfaitement faire rfrence lide de vent, comme dans le compos taif, typhon. Pour un compos, il convient donc dabord didentifier globalement le mot souvent deux kanjis puis den dduire les lectures de chaque kanji. Cela ne supprime cependant pas toutes les ambigits, comme avec les composs suivants Exemples de composs ayant plusieurs lectures1. ComposLecture sens. Lecture sens. Remarqueskamei pseudonymekana syllabaire japonaisakago bbsekishi peuple du point de vue dun monarchenanibito quiconquenannin combien de personnes. Il existe galement la lecture nanpito, synonyme de nanibito. gosho palais imprial. Gose ville du centre du Japonichiji une heure du matin ou de laprs midi, pour un tempsittoki pour un temps. On voit dans cet exemple que les sens associs des lectures disctinctes peuvent tre partiellement ou entirement similaires. Les lectures on des kanjis drivent des prononciations originelles chinoises mais la correspondance nest gnralement pas directe entre la prononciation moderne et son origine chinoise. Cette prononciation dorigine na t quapproximativement rendue dans le systme phontique japonais, trs diffrent de ceux de la Chine, ignorant notamment les tons. De plus, le systme phontique japonais, bien que relativement assez stable, a lui mme connu quelques volutions travers les sicles.
Par exemple, sakaki, qui dsigne un arbre sacr dans la religion shinto, est un kanji apparu au Japon il provient de la fusion des caractres et, respectivement arbre et divinit 9. Les kanjis tant lorigine des caractres reprsentant des mots ou morphmes chinois, et non japonais, leur introduction pour transcrire la langue japonaise ne conduisit pas une lecture univoque. Les prononciations associes en Chine aux sinogrammes ont donn ce quon appelle les lectures sino japonaises on en japonais onyomi voir le sinogramme le son. Aprs limportation de caractres ou concepts chinois, la langue japonaise a souvent conserv la mmoire de ces prononciations trangres, mmoire qui a nanmoins pu voluer depuis, suivant lvolution phontique du japonais. Quand le concept existait en japonais, il put aussi tre traduit et vocalis suivant les mots de la langue nipponne originelle, la lecture du caractre se faisant donc la japonaise ces lectures sont dites kun en japonais kunyomi voir le sinogramme instruire, exgse. La plupart des kanjis a de ce fait au moins deux lectures possibles on et kun. Ce nest toutefois pas une rgle absolue, et lon trouve des kanjis sans lecture kun comme kiku, chrysanthme, ou sans lecture on comme iwashi, sardine labsence de lecture on est videmment frquente pour les kanjis crs au Japon, les kokuji. Pour les mots composs de deux kanjis ou plus, jukugo, les lectures hybrides abondent. Par exemple, en cuisine, gy niku, buf et y niku, mouton ont une lecture de type on on, mais buta niku, porc et tori niku, volaille ont en revanche des lectures kun on ces dernires lectures sont qualifies de lectures yut, yutyomi. Hormis le cas simple des caractre nayant quune seule lecture, on ou kun selon les cas, la majorit des kanjis rencontrs dans les textes japonais sont pourvus de deux lectures ou davantage. Ainsi, certains kanjis dusage courant peuvent avoir plus dune dizaine de lectures possibles. On trouve par exemple le kanji signifiant notamment la vie ou vivre dont les lectures officielles sont sei, sh, i kasu1. Souvent, donc, dterminer la lecture dun kanji suppose davoir identifi correctement le sens dans lequel il est employ. Il faut pour cela observer un ou plusieurs signes situs son voisinage, voire juger plus largement en fonction du contexte. Par exemple, lhomographe peut soit faire rfrence au mot kaze vent soit au mot f apparence, style il est donc ncessaire de deviner en amont, par le contexte, la valeur smantique de pour pouvoir le lire. Dautre part, dans les mots composs contenant, cette nette distinction disparait, la lecture f pouvant parfaitement faire rfrence lide de vent, comme dans le compos taif, typhon. Pour un compos, il convient donc dabord didentifier globalement le mot souvent deux kanjis puis den dduire les lectures de chaque kanji. Cela ne supprime cependant pas toutes les ambigits, comme avec les composs suivants Exemples de composs ayant plusieurs lectures1. ComposLecture sens. Lecture sens. Remarqueskamei pseudonymekana syllabaire japonaisakago bbsekishi peuple du point de vue dun monarchenanibito quiconquenannin combien de personnes. Il existe galement la lecture nanpito, synonyme de nanibito. gosho palais imprial. Gose ville du centre du Japonichiji une heure du matin ou de laprs midi, pour un tempsittoki pour un temps. On voit dans cet exemple que les sens associs des lectures disctinctes peuvent tre partiellement ou entirement similaires. Les lectures on des kanjis drivent des prononciations originelles chinoises mais la correspondance nest gnralement pas directe entre la prononciation moderne et son origine chinoise. Cette prononciation dorigine na t quapproximativement rendue dans le systme phontique japonais, trs diffrent de ceux de la Chine, ignorant notamment les tons. De plus, le systme phontique japonais, bien que relativement assez stable, a lui mme connu quelques volutions travers les sicles.


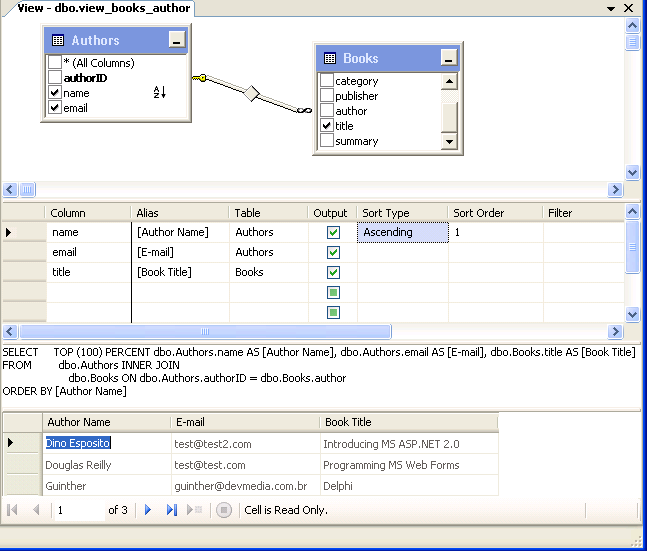
 Restauracin de bases de datos maestras de Microsoft SQL Server 7. 65 Proteger Microsoft Windows SharePoint Services. Download the free trial version below to get started. Doubleclick the downloaded file to install the software.
Restauracin de bases de datos maestras de Microsoft SQL Server 7. 65 Proteger Microsoft Windows SharePoint Services. Download the free trial version below to get started. Doubleclick the downloaded file to install the software. 
 Kanji Font EnglishHub. Most of the language data and media files used in Kanji alive are freely available under a Creative Commons CC BY license. StrokeRadical. Position. Meaning. Reading. Notes. Importance. Important. 2person2persona variant of Important. Important. 2human legsImportant.
Kanji Font EnglishHub. Most of the language data and media files used in Kanji alive are freely available under a Creative Commons CC BY license. StrokeRadical. Position. Meaning. Reading. Notes. Importance. Important. 2person2persona variant of Important. Important. 2human legsImportant.  Important. 2ice2table2winda variant of 2container, open box2knife, sword2knife, sworda variant of Important. Important. 2private, Katakana Mu2again, right hand3mouth3moutha variant of Important. Important. 3earth3eartha variant of Important. Important. 3child, son3child, sona variant of Important. Important. 3inch, 2. Important. 3to move, stretch3folded hands3javelin3bow in archery3bow in archerya variant of 3pigs head3pigs heada variant of 3pigs heada variant of 3hair style, light rays3step, stride, street, to goImportant. Important. 3road, walk, to advancea variant of Important. Important. 3hill, mounda variant of Important. Katakana Tsu3heart, mind, spirita variant of Important. Important. 3watera variant of Important. Important. 4heart, mind, spirit4heart, mind, spirita variant of 4spear, weapon4door4doora variant of 4hand4branch4activity, to strike, hit4activity, to strike, hita variant of Important. Important. 4to say4moon, month, period4moon, month, perioda variant of 4meat, flesha variant of Important. Important. 4to lack, yawn4to stop4death dying, to decompose4death dying, to decomposea variant of 4lance shaft, action4not, mother4to compare4hair4family, clan4steam, air4water4fire4firea variant of Important. Important. 4claw, nail4claw, naila variant of 4claw, naila variant of 4father4to mix4split wood4split wood4split wooda variant of 4fang, canine tooth4cow4cowa variant of 4dog4jewelry, jeweled kinga variant of Important.
Important. 2ice2table2winda variant of 2container, open box2knife, sword2knife, sworda variant of Important. Important. 2private, Katakana Mu2again, right hand3mouth3moutha variant of Important. Important. 3earth3eartha variant of Important. Important. 3child, son3child, sona variant of Important. Important. 3inch, 2. Important. 3to move, stretch3folded hands3javelin3bow in archery3bow in archerya variant of 3pigs head3pigs heada variant of 3pigs heada variant of 3hair style, light rays3step, stride, street, to goImportant. Important. 3road, walk, to advancea variant of Important. Important. 3hill, mounda variant of Important. Katakana Tsu3heart, mind, spirita variant of Important. Important. 3watera variant of Important. Important. 4heart, mind, spirit4heart, mind, spirita variant of 4spear, weapon4door4doora variant of 4hand4branch4activity, to strike, hit4activity, to strike, hita variant of Important. Important. 4to say4moon, month, period4moon, month, perioda variant of 4meat, flesha variant of Important. Important. 4to lack, yawn4to stop4death dying, to decompose4death dying, to decomposea variant of 4lance shaft, action4not, mother4to compare4hair4family, clan4steam, air4water4fire4firea variant of Important. Important. 4claw, nail4claw, naila variant of 4claw, naila variant of 4father4to mix4split wood4split wood4split wooda variant of 4fang, canine tooth4cow4cowa variant of 4dog4jewelry, jeweled kinga variant of Important.  Shodo Japanese calligraphy Youve seen people with tattoos of kanji symbols. Youve seen bookmarks and mood stones. The beauty and simplicity of Shodo Japanese. Important. 4neta variant of 4old, old agea variant of 5darkness5jewelry5melon5tile5sweet5birth, to be born, live5to use5rice paddy5rice paddya variant of 5bolt of cloth5bolt of clotha variant of 5sicknessImportant. Important. 5eyea variant of 5halberd5halberda variant of 5arrow5arrowa variant of 5stone5stonea variant of 5altar, festival, religious service5footprint5grainImportant. Important. 5to stand5to standa variant of 5fang, canine tootha variant of 5fang, canine tootha variant of 5watera variant of 5neta variant of 5neta variant of 5clothinga variant of Important. Important. 6rice6ricea variant of Important. Important. 6earthen jar6net6sheep6sheepa variant of 6feather, wing6feather, winga variant of 6old, old age6and also6plow6ear6eara variant of 6writing brush6flesh, meat6retainer, minister6self6to arrive, reach6to arrive, reacha variant of 6mortar, quern6tongue6contrary, to err6ship, boat6ship, boata variant of 6boundary6color6grass, plant6tiger6worm, insect, bug6worm, insect, buga variant of Important. Important. 6clothing6cover, west6cover, westa variant of 6melona variant of 7to see7horn, corner7horn, cornera variant of 7words, to speak, say7words, to speak, saya variant of Important. Important. 7red7to run7to runa variant of Important. Kanji Wikipdia. Les kanjis1 sont des caractres chinois dont la fonction est dcrire une partie de la langue japonaise en associant chaque signe une matrice de sens signifis et de lectures valeurs phonologiques. Le mot kanji vient du japonais romaniskanji, qui est la transcription du terme un mot compos prcisment de deux kanjis. Il sagit de caractres, ji utiles lcriture du japonais, qui ont t emprunts pour la plupart au systme dcriture de lethnie chinoise han, kan littralement donc des caractres chinois ou sinogrammes 2. Les kanjis forment lun des grands ensembles de caractres mojishu de lcriture au Japon, avec dune part les kanas, syllabaires3 spcifiquement japonais composs des hiraganas et katakanas, et, dautre part, les emprunts au monde occidental, savoir les lettres latines rmaji et les chiffres arabes. Lorigine des kanjis est, par dfinition, celle de lcriture dveloppe dans la Chine antique laquelle dbute, si on se limite aux plus anciens documents connus, avec lcriture osscaille la fin de la dynastie Shang. Quant lpoque de limportation des sinogrammes au Japon, celle ci nest pas connue avec exactitude le Kojiki 7. Archipel. Par ailleurs, la tradition considre que lon doit lenseignement des caractres chinois auprs de la cour impriale japonaise au lettr Wani, venu du royaume de Baekje5. La caractristique la plus remarquable des kanjis, comme des sinogrammes en gnral, est le lien quil existe entre chaque signe et un ensemble de sens jigi, lien qui dcoule de la nature logographique des sinogrammes, chacun de ces derniers codant gnralement un mot ou un morphme de la langue chinoise antique. Cela les oppose, par exemple, aux lettres latines ou aux kanas, qui ne reprsentent intrinsquement que des sons. Dans le modle de lcriture japonaise mlant kanjis et kanas kanji kana majiribun6, les kanjis sont gnralement utiliss pour crire la racine des mots, lhabillage grammatical de la phrase tant crit en syllabaires7 hiraganas. En outre, sur le plan de sa prononciation, cette criture nest pas univoque, car un mme kanji dans la langue crite peut souvent se raliser de diffrentes manires dans la langue orale on parle de ses diffrentes lectures, en japonais yomi ou onkun8, qui correspondent chacunes une ou plusieurs mores. Le fait que ces caractres sont inclus dans un ensemble dsign sous le terme gnrique de caractres chinois ne doit pas se comprendre comme une simple inclusion des kanjis dans un systme scriptural purement chinois ce qui constitue nanmoins une bonne premire approximation. Kanji Font DownloadEn plus du fait que les lectures des kanjis se distinguent des lectures observes au sein des langues chinoises, il existe un nombre important de spcificits nipponnes quant lapparence graphique voire aux valeurs smantiques des kanjis ces points seront plus amplement dtaills dans la suite de larticle. Dautre part, il est intressant de noter quil existe, de surcroit, une petite proportion de kanjis dits nationaux , kokuji, qui sont ns au Japon.
Shodo Japanese calligraphy Youve seen people with tattoos of kanji symbols. Youve seen bookmarks and mood stones. The beauty and simplicity of Shodo Japanese. Important. 4neta variant of 4old, old agea variant of 5darkness5jewelry5melon5tile5sweet5birth, to be born, live5to use5rice paddy5rice paddya variant of 5bolt of cloth5bolt of clotha variant of 5sicknessImportant. Important. 5eyea variant of 5halberd5halberda variant of 5arrow5arrowa variant of 5stone5stonea variant of 5altar, festival, religious service5footprint5grainImportant. Important. 5to stand5to standa variant of 5fang, canine tootha variant of 5fang, canine tootha variant of 5watera variant of 5neta variant of 5neta variant of 5clothinga variant of Important. Important. 6rice6ricea variant of Important. Important. 6earthen jar6net6sheep6sheepa variant of 6feather, wing6feather, winga variant of 6old, old age6and also6plow6ear6eara variant of 6writing brush6flesh, meat6retainer, minister6self6to arrive, reach6to arrive, reacha variant of 6mortar, quern6tongue6contrary, to err6ship, boat6ship, boata variant of 6boundary6color6grass, plant6tiger6worm, insect, bug6worm, insect, buga variant of Important. Important. 6clothing6cover, west6cover, westa variant of 6melona variant of 7to see7horn, corner7horn, cornera variant of 7words, to speak, say7words, to speak, saya variant of Important. Important. 7red7to run7to runa variant of Important. Kanji Wikipdia. Les kanjis1 sont des caractres chinois dont la fonction est dcrire une partie de la langue japonaise en associant chaque signe une matrice de sens signifis et de lectures valeurs phonologiques. Le mot kanji vient du japonais romaniskanji, qui est la transcription du terme un mot compos prcisment de deux kanjis. Il sagit de caractres, ji utiles lcriture du japonais, qui ont t emprunts pour la plupart au systme dcriture de lethnie chinoise han, kan littralement donc des caractres chinois ou sinogrammes 2. Les kanjis forment lun des grands ensembles de caractres mojishu de lcriture au Japon, avec dune part les kanas, syllabaires3 spcifiquement japonais composs des hiraganas et katakanas, et, dautre part, les emprunts au monde occidental, savoir les lettres latines rmaji et les chiffres arabes. Lorigine des kanjis est, par dfinition, celle de lcriture dveloppe dans la Chine antique laquelle dbute, si on se limite aux plus anciens documents connus, avec lcriture osscaille la fin de la dynastie Shang. Quant lpoque de limportation des sinogrammes au Japon, celle ci nest pas connue avec exactitude le Kojiki 7. Archipel. Par ailleurs, la tradition considre que lon doit lenseignement des caractres chinois auprs de la cour impriale japonaise au lettr Wani, venu du royaume de Baekje5. La caractristique la plus remarquable des kanjis, comme des sinogrammes en gnral, est le lien quil existe entre chaque signe et un ensemble de sens jigi, lien qui dcoule de la nature logographique des sinogrammes, chacun de ces derniers codant gnralement un mot ou un morphme de la langue chinoise antique. Cela les oppose, par exemple, aux lettres latines ou aux kanas, qui ne reprsentent intrinsquement que des sons. Dans le modle de lcriture japonaise mlant kanjis et kanas kanji kana majiribun6, les kanjis sont gnralement utiliss pour crire la racine des mots, lhabillage grammatical de la phrase tant crit en syllabaires7 hiraganas. En outre, sur le plan de sa prononciation, cette criture nest pas univoque, car un mme kanji dans la langue crite peut souvent se raliser de diffrentes manires dans la langue orale on parle de ses diffrentes lectures, en japonais yomi ou onkun8, qui correspondent chacunes une ou plusieurs mores. Le fait que ces caractres sont inclus dans un ensemble dsign sous le terme gnrique de caractres chinois ne doit pas se comprendre comme une simple inclusion des kanjis dans un systme scriptural purement chinois ce qui constitue nanmoins une bonne premire approximation. Kanji Font DownloadEn plus du fait que les lectures des kanjis se distinguent des lectures observes au sein des langues chinoises, il existe un nombre important de spcificits nipponnes quant lapparence graphique voire aux valeurs smantiques des kanjis ces points seront plus amplement dtaills dans la suite de larticle. Dautre part, il est intressant de noter quil existe, de surcroit, une petite proportion de kanjis dits nationaux , kokuji, qui sont ns au Japon.  Par exemple, sakaki, qui dsigne un arbre sacr dans la religion shinto, est un kanji apparu au Japon il provient de la fusion des caractres et, respectivement arbre et divinit 9. Les kanjis tant lorigine des caractres reprsentant des mots ou morphmes chinois, et non japonais, leur introduction pour transcrire la langue japonaise ne conduisit pas une lecture univoque. Les prononciations associes en Chine aux sinogrammes ont donn ce quon appelle les lectures sino japonaises on en japonais onyomi voir le sinogramme le son. Aprs limportation de caractres ou concepts chinois, la langue japonaise a souvent conserv la mmoire de ces prononciations trangres, mmoire qui a nanmoins pu voluer depuis, suivant lvolution phontique du japonais. Quand le concept existait en japonais, il put aussi tre traduit et vocalis suivant les mots de la langue nipponne originelle, la lecture du caractre se faisant donc la japonaise ces lectures sont dites kun en japonais kunyomi voir le sinogramme instruire, exgse. La plupart des kanjis a de ce fait au moins deux lectures possibles on et kun. Ce nest toutefois pas une rgle absolue, et lon trouve des kanjis sans lecture kun comme kiku, chrysanthme, ou sans lecture on comme iwashi, sardine labsence de lecture on est videmment frquente pour les kanjis crs au Japon, les kokuji. Pour les mots composs de deux kanjis ou plus, jukugo, les lectures hybrides abondent. Par exemple, en cuisine, gy niku, buf et y niku, mouton ont une lecture de type on on, mais buta niku, porc et tori niku, volaille ont en revanche des lectures kun on ces dernires lectures sont qualifies de lectures yut, yutyomi. Hormis le cas simple des caractre nayant quune seule lecture, on ou kun selon les cas, la majorit des kanjis rencontrs dans les textes japonais sont pourvus de deux lectures ou davantage. Ainsi, certains kanjis dusage courant peuvent avoir plus dune dizaine de lectures possibles. On trouve par exemple le kanji signifiant notamment la vie ou vivre dont les lectures officielles sont sei, sh, i kasu1. Souvent, donc, dterminer la lecture dun kanji suppose davoir identifi correctement le sens dans lequel il est employ. Il faut pour cela observer un ou plusieurs signes situs son voisinage, voire juger plus largement en fonction du contexte. Par exemple, lhomographe peut soit faire rfrence au mot kaze vent soit au mot f apparence, style il est donc ncessaire de deviner en amont, par le contexte, la valeur smantique de pour pouvoir le lire. Dautre part, dans les mots composs contenant, cette nette distinction disparait, la lecture f pouvant parfaitement faire rfrence lide de vent, comme dans le compos taif, typhon. Pour un compos, il convient donc dabord didentifier globalement le mot souvent deux kanjis puis den dduire les lectures de chaque kanji. Cela ne supprime cependant pas toutes les ambigits, comme avec les composs suivants Exemples de composs ayant plusieurs lectures1. ComposLecture sens. Lecture sens. Remarqueskamei pseudonymekana syllabaire japonaisakago bbsekishi peuple du point de vue dun monarchenanibito quiconquenannin combien de personnes. Il existe galement la lecture nanpito, synonyme de nanibito. gosho palais imprial. Gose ville du centre du Japonichiji une heure du matin ou de laprs midi, pour un tempsittoki pour un temps. On voit dans cet exemple que les sens associs des lectures disctinctes peuvent tre partiellement ou entirement similaires. Les lectures on des kanjis drivent des prononciations originelles chinoises mais la correspondance nest gnralement pas directe entre la prononciation moderne et son origine chinoise. Cette prononciation dorigine na t quapproximativement rendue dans le systme phontique japonais, trs diffrent de ceux de la Chine, ignorant notamment les tons. De plus, le systme phontique japonais, bien que relativement assez stable, a lui mme connu quelques volutions travers les sicles.
Par exemple, sakaki, qui dsigne un arbre sacr dans la religion shinto, est un kanji apparu au Japon il provient de la fusion des caractres et, respectivement arbre et divinit 9. Les kanjis tant lorigine des caractres reprsentant des mots ou morphmes chinois, et non japonais, leur introduction pour transcrire la langue japonaise ne conduisit pas une lecture univoque. Les prononciations associes en Chine aux sinogrammes ont donn ce quon appelle les lectures sino japonaises on en japonais onyomi voir le sinogramme le son. Aprs limportation de caractres ou concepts chinois, la langue japonaise a souvent conserv la mmoire de ces prononciations trangres, mmoire qui a nanmoins pu voluer depuis, suivant lvolution phontique du japonais. Quand le concept existait en japonais, il put aussi tre traduit et vocalis suivant les mots de la langue nipponne originelle, la lecture du caractre se faisant donc la japonaise ces lectures sont dites kun en japonais kunyomi voir le sinogramme instruire, exgse. La plupart des kanjis a de ce fait au moins deux lectures possibles on et kun. Ce nest toutefois pas une rgle absolue, et lon trouve des kanjis sans lecture kun comme kiku, chrysanthme, ou sans lecture on comme iwashi, sardine labsence de lecture on est videmment frquente pour les kanjis crs au Japon, les kokuji. Pour les mots composs de deux kanjis ou plus, jukugo, les lectures hybrides abondent. Par exemple, en cuisine, gy niku, buf et y niku, mouton ont une lecture de type on on, mais buta niku, porc et tori niku, volaille ont en revanche des lectures kun on ces dernires lectures sont qualifies de lectures yut, yutyomi. Hormis le cas simple des caractre nayant quune seule lecture, on ou kun selon les cas, la majorit des kanjis rencontrs dans les textes japonais sont pourvus de deux lectures ou davantage. Ainsi, certains kanjis dusage courant peuvent avoir plus dune dizaine de lectures possibles. On trouve par exemple le kanji signifiant notamment la vie ou vivre dont les lectures officielles sont sei, sh, i kasu1. Souvent, donc, dterminer la lecture dun kanji suppose davoir identifi correctement le sens dans lequel il est employ. Il faut pour cela observer un ou plusieurs signes situs son voisinage, voire juger plus largement en fonction du contexte. Par exemple, lhomographe peut soit faire rfrence au mot kaze vent soit au mot f apparence, style il est donc ncessaire de deviner en amont, par le contexte, la valeur smantique de pour pouvoir le lire. Dautre part, dans les mots composs contenant, cette nette distinction disparait, la lecture f pouvant parfaitement faire rfrence lide de vent, comme dans le compos taif, typhon. Pour un compos, il convient donc dabord didentifier globalement le mot souvent deux kanjis puis den dduire les lectures de chaque kanji. Cela ne supprime cependant pas toutes les ambigits, comme avec les composs suivants Exemples de composs ayant plusieurs lectures1. ComposLecture sens. Lecture sens. Remarqueskamei pseudonymekana syllabaire japonaisakago bbsekishi peuple du point de vue dun monarchenanibito quiconquenannin combien de personnes. Il existe galement la lecture nanpito, synonyme de nanibito. gosho palais imprial. Gose ville du centre du Japonichiji une heure du matin ou de laprs midi, pour un tempsittoki pour un temps. On voit dans cet exemple que les sens associs des lectures disctinctes peuvent tre partiellement ou entirement similaires. Les lectures on des kanjis drivent des prononciations originelles chinoises mais la correspondance nest gnralement pas directe entre la prononciation moderne et son origine chinoise. Cette prononciation dorigine na t quapproximativement rendue dans le systme phontique japonais, trs diffrent de ceux de la Chine, ignorant notamment les tons. De plus, le systme phontique japonais, bien que relativement assez stable, a lui mme connu quelques volutions travers les sicles. 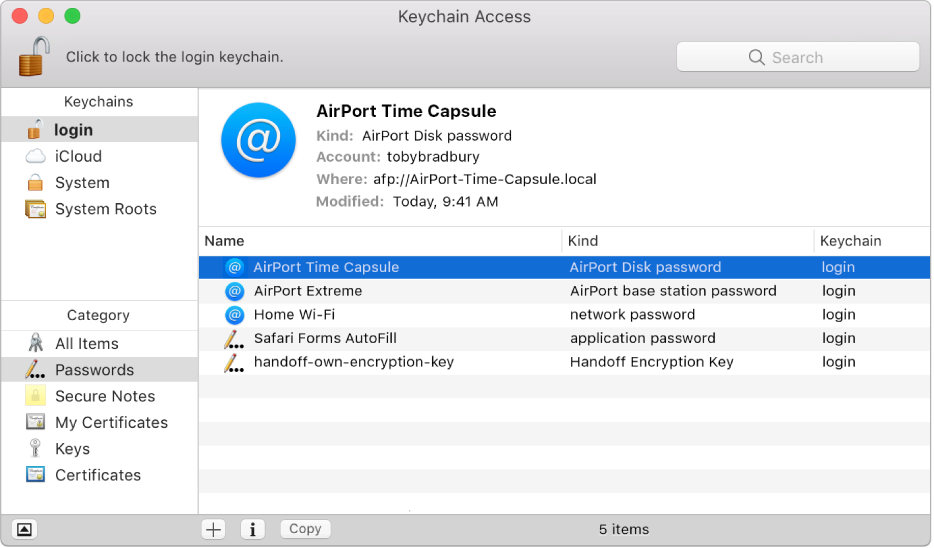
 Migrating saved website and terminal services passwords with Windows 7 Credential Manager. Credential Manager, a new item that you may have noticed in the Windows 7 control panel, stores login and password info that you have chosen to save. Credential manager stores Website passwords. Terminal Services Remote Desktop passwords. Runas credentials. Workgroup shared resource credentials. It works in a similar way to the Keychain Access application included with Mac OS X and you will be able to use it to store passwords for future applications that are written for Windows 7. It also works with a number of todays applications. A cool feature of Credential Manager is the ability to update authentication details, changing login and password details as necessary. This vastly simplifies the process of rotating your passwords for all the web services you access. A big security risk people face is that they often use the same username and password combination for each forum or social networking site that they visit.
Migrating saved website and terminal services passwords with Windows 7 Credential Manager. Credential Manager, a new item that you may have noticed in the Windows 7 control panel, stores login and password info that you have chosen to save. Credential manager stores Website passwords. Terminal Services Remote Desktop passwords. Runas credentials. Workgroup shared resource credentials. It works in a similar way to the Keychain Access application included with Mac OS X and you will be able to use it to store passwords for future applications that are written for Windows 7. It also works with a number of todays applications. A cool feature of Credential Manager is the ability to update authentication details, changing login and password details as necessary. This vastly simplifies the process of rotating your passwords for all the web services you access. A big security risk people face is that they often use the same username and password combination for each forum or social networking site that they visit.  That means that there only has to be a security breach at one forum and the passwords for all forums are lost. With credential manager you can use unique password for all forums and then update them without having to go through the hassle of having to have an e mail sent out to you to remind you of what your old complex password was. My favorite part of Credential Manager is that it allows you to backup all the credentials used on one computer and transfer them to another computer. I use complex passwords that are almost impossible to remember, which means that I tend to use certain web services on certain computers because I cant remember the credential information so that I can log on to that service from another computer. Credential manager allows me to by backing up the Windows Vault and then restoring it on another computer allowing me to ensure that each of my computers running Windows 7 and I use a number of them has access to the same set of stored credentials. The backup process is secured by forcing you to the secure desktop when entering the password used to encrypt the exported Windows Vault.
That means that there only has to be a security breach at one forum and the passwords for all forums are lost. With credential manager you can use unique password for all forums and then update them without having to go through the hassle of having to have an e mail sent out to you to remind you of what your old complex password was. My favorite part of Credential Manager is that it allows you to backup all the credentials used on one computer and transfer them to another computer. I use complex passwords that are almost impossible to remember, which means that I tend to use certain web services on certain computers because I cant remember the credential information so that I can log on to that service from another computer. Credential manager allows me to by backing up the Windows Vault and then restoring it on another computer allowing me to ensure that each of my computers running Windows 7 and I use a number of them has access to the same set of stored credentials. The backup process is secured by forcing you to the secure desktop when entering the password used to encrypt the exported Windows Vault.  You must go through the same secure desktop process to import the passwords on the destination computer. Credential Manager is one of those small but cool features Ive been waiting for. As I mentioned earlier, getting people to use separate complex passwords for the different websites that they use can be hard. They end up using the same password for all websites, which is a really big security risk. Credential Manager takes the hassle out of remembering complex passwords. It is a nifty feature and one that makes it hard to switch back to computers running earlier Windows operating systems.
You must go through the same secure desktop process to import the passwords on the destination computer. Credential Manager is one of those small but cool features Ive been waiting for. As I mentioned earlier, getting people to use separate complex passwords for the different websites that they use can be hard. They end up using the same password for all websites, which is a really big security risk. Credential Manager takes the hassle out of remembering complex passwords. It is a nifty feature and one that makes it hard to switch back to computers running earlier Windows operating systems.  How to Change the Password in Keychain Access Mac. Hey mac users, Keychain Access is a Mac OS X application that allows the user to access the Apple Keychain and. When you turn on iCloud Photo Library, every photo you take is automatically uploaded in full resolution. And any edits you make are automatically updated everywhere. Find out how to access your iCloud photos, videos, music, and even documents apps anywhere with iCloud drive. Ive generated key pairs using PuttyGen and been logging in using Pageant, so that I have to enter my passphrase only once when my system boots. How do I achieve.
How to Change the Password in Keychain Access Mac. Hey mac users, Keychain Access is a Mac OS X application that allows the user to access the Apple Keychain and. When you turn on iCloud Photo Library, every photo you take is automatically uploaded in full resolution. And any edits you make are automatically updated everywhere. Find out how to access your iCloud photos, videos, music, and even documents apps anywhere with iCloud drive. Ive generated key pairs using PuttyGen and been logging in using Pageant, so that I have to enter my passphrase only once when my system boots. How do I achieve. 
 Phone 8, capable of recording in 4. K, or a Nexus 5 from 2. You shouldnt purchase a smartphone exclusively for action camera action, though its a pretty functional substitute. That HD camera, combined with a selection of video editing apps, means you can record, edit, and upload your stunts all from the same device, rather than depending on two devices to handle the job. Larger smartphones, like the i. Phone 7 Plus, feature optical image stabilization as well, so your videos wont look too choppy. If you have a Go. Pro and a DSLR camera, you may want to use both of them at the same time to capture Read more Read. If you already have a smartphone, turning it into an action camera is pretty easy just buy a case, a mount, and open your camera app. If youre looking for a particular Go.
Phone 8, capable of recording in 4. K, or a Nexus 5 from 2. You shouldnt purchase a smartphone exclusively for action camera action, though its a pretty functional substitute. That HD camera, combined with a selection of video editing apps, means you can record, edit, and upload your stunts all from the same device, rather than depending on two devices to handle the job. Larger smartphones, like the i. Phone 7 Plus, feature optical image stabilization as well, so your videos wont look too choppy. If you have a Go. Pro and a DSLR camera, you may want to use both of them at the same time to capture Read more Read. If you already have a smartphone, turning it into an action camera is pretty easy just buy a case, a mount, and open your camera app. If youre looking for a particular Go.  Pro mount like one for your dog youll find a corresponding version for your mobile device. Youll need a case that can fit inside the mounts, but companies like Otterbox make cases with mounting capabilities that are designed to take a tumble. Of course, if you hit the pavement along with your Pixel in the wrong way, theres the tiny chance your screen will turn into a kaleidoscope of color and broken glass. Seems a little risky. Verdict Got the CashGet a Go. Pro. In the end, the compact size, durability, and single purpose use case of the Go. Pro action camera make it the ideal action camera, even when youve got a phone in your pocket. Its one touch recording capabilities make it simple to grab and go, and youre bound to fret less about it falling on the asphalt when compared to your thin, action averse smartphone in a bulky case. If money is a concern, buy a helmet mount for your device and test it out, at least to see if you like it. But if youre doing anything more than riding your bike to work, and want to capture the spectacle, get yourself a Go. Pro and go big or go home. All pictures and text in these pages are c2016 VVVintage Vintage Bicycles, Inc. tm and may not be used in any form without written permission from VVVintage. Raleigh Serial Numbers Charts. Serial convention.
Pro mount like one for your dog youll find a corresponding version for your mobile device. Youll need a case that can fit inside the mounts, but companies like Otterbox make cases with mounting capabilities that are designed to take a tumble. Of course, if you hit the pavement along with your Pixel in the wrong way, theres the tiny chance your screen will turn into a kaleidoscope of color and broken glass. Seems a little risky. Verdict Got the CashGet a Go. Pro. In the end, the compact size, durability, and single purpose use case of the Go. Pro action camera make it the ideal action camera, even when youve got a phone in your pocket. Its one touch recording capabilities make it simple to grab and go, and youre bound to fret less about it falling on the asphalt when compared to your thin, action averse smartphone in a bulky case. If money is a concern, buy a helmet mount for your device and test it out, at least to see if you like it. But if youre doing anything more than riding your bike to work, and want to capture the spectacle, get yourself a Go. Pro and go big or go home. All pictures and text in these pages are c2016 VVVintage Vintage Bicycles, Inc. tm and may not be used in any form without written permission from VVVintage. Raleigh Serial Numbers Charts. Serial convention.  At present, I have insufficent information about the serial numbers from this era to construct a definite chart of every example used during this time period. At least 4 or 5 different systems were used. I have uncovered two of them to a reasonable extent both of which ran concurrently to each other during this time period. System 1. 97. 0 The first system consists of 7 digits, beginning with 1. This system showed its face in 1. I have named it accordingly, and was phased out in mid 1. EXCEPTIONS Evidence indicates that a handful of 7. This is the only explanation I can suggest regarding this issue. System 1. 97. 2 A second 5 6 digit serial system was introduced in 1. NO rhyme or reason, and died a quick death before 1. This system never exeeded 6 digits, and the reason for its introduction remains a mystery. Regardless, it is here, and it will stay. This system INCLUDES the Grand Prix and Super Course, despite the seven digit serials as mentioned in the next system, below running concurrently on these models. Serial location. The serials from this era, specifically for general production machines Sports, Superbe, Sprite, will be located on the seat lug. TwentyFolders will have the serial marked on the outside of the left dropout, and some Grand Prix models have it in this location as well. Unknown where they are located on DL 1s. Keep in mind that the serials used for Raleigh Choppers while apparently a nearly identical 7 digit system do not corrispond well with those of the larger bicycles. For now, it should be assumed that the Choppers serial system is separate until proven otherwise. Mens models will have the stamping on the top of the lug, ladies frames will have the serial stamped to the front of the lug. Addendums and warnings. Both of these systems are often covered deep in paint do not be surprised if you only find 5 or 6 digits Given the obvious duplication of serials with bikes produced prior to 1. Raleigh Sports Visual ID page for this purpose. Please understand that this particular chart is a rough draft. Use in conjunction with Sturmey Archer rear hubs and frameset decals as additional guides. All of the serial cutoffs are approximated. Please allow for overlap.
At present, I have insufficent information about the serial numbers from this era to construct a definite chart of every example used during this time period. At least 4 or 5 different systems were used. I have uncovered two of them to a reasonable extent both of which ran concurrently to each other during this time period. System 1. 97. 0 The first system consists of 7 digits, beginning with 1. This system showed its face in 1. I have named it accordingly, and was phased out in mid 1. EXCEPTIONS Evidence indicates that a handful of 7. This is the only explanation I can suggest regarding this issue. System 1. 97. 2 A second 5 6 digit serial system was introduced in 1. NO rhyme or reason, and died a quick death before 1. This system never exeeded 6 digits, and the reason for its introduction remains a mystery. Regardless, it is here, and it will stay. This system INCLUDES the Grand Prix and Super Course, despite the seven digit serials as mentioned in the next system, below running concurrently on these models. Serial location. The serials from this era, specifically for general production machines Sports, Superbe, Sprite, will be located on the seat lug. TwentyFolders will have the serial marked on the outside of the left dropout, and some Grand Prix models have it in this location as well. Unknown where they are located on DL 1s. Keep in mind that the serials used for Raleigh Choppers while apparently a nearly identical 7 digit system do not corrispond well with those of the larger bicycles. For now, it should be assumed that the Choppers serial system is separate until proven otherwise. Mens models will have the stamping on the top of the lug, ladies frames will have the serial stamped to the front of the lug. Addendums and warnings. Both of these systems are often covered deep in paint do not be surprised if you only find 5 or 6 digits Given the obvious duplication of serials with bikes produced prior to 1. Raleigh Sports Visual ID page for this purpose. Please understand that this particular chart is a rough draft. Use in conjunction with Sturmey Archer rear hubs and frameset decals as additional guides. All of the serial cutoffs are approximated. Please allow for overlap. /DIR-600L_Datasheet_US-1.jpg)
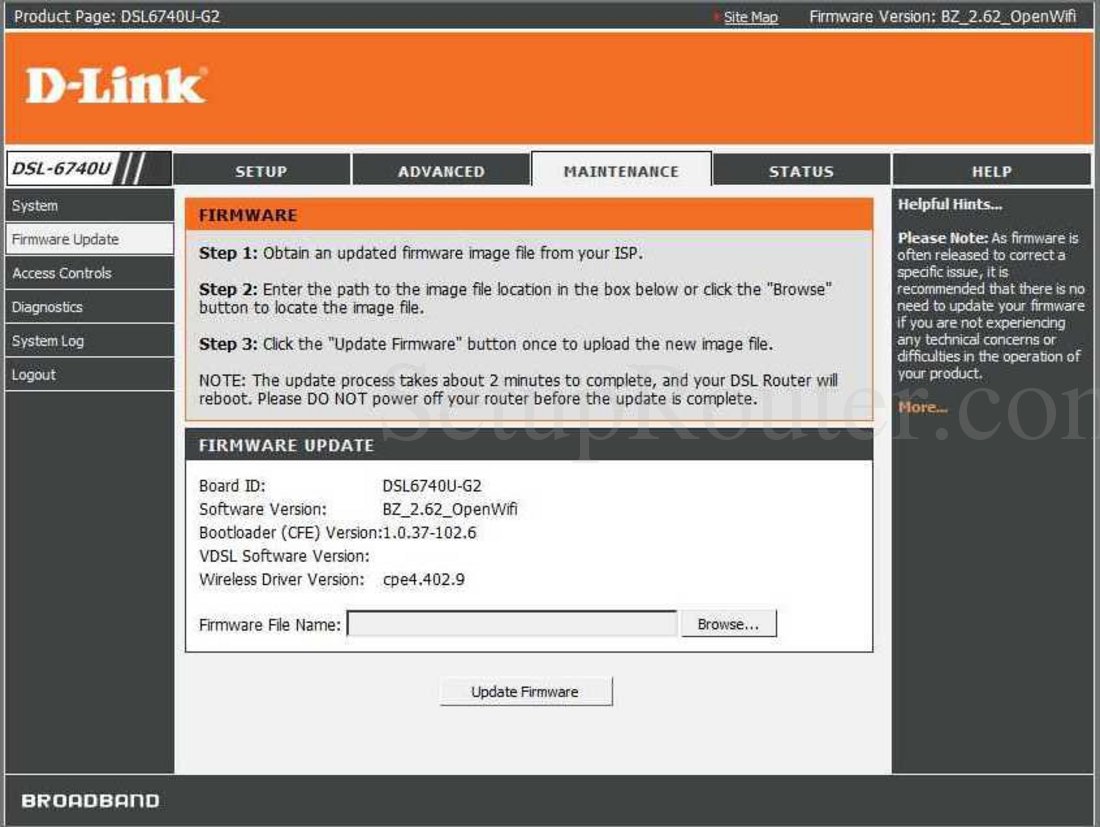 Email Settings. The Email feature can be used to send the system log files, router alert messages, and firmware update notification to your email address. Manual Revision A Firmware Manual Revision B Firmware. If youve got a DLink DIR850L AC1200 router, its time to think about replacing it the holes in the firmware might never be fixed. Researcher discloses 10 DLink zeroday router flaws. The security researcher says the general public should immediately disconnect their router until patches are.
Email Settings. The Email feature can be used to send the system log files, router alert messages, and firmware update notification to your email address. Manual Revision A Firmware Manual Revision B Firmware. If youve got a DLink DIR850L AC1200 router, its time to think about replacing it the holes in the firmware might never be fixed. Researcher discloses 10 DLink zeroday router flaws. The security researcher says the general public should immediately disconnect their router until patches are. 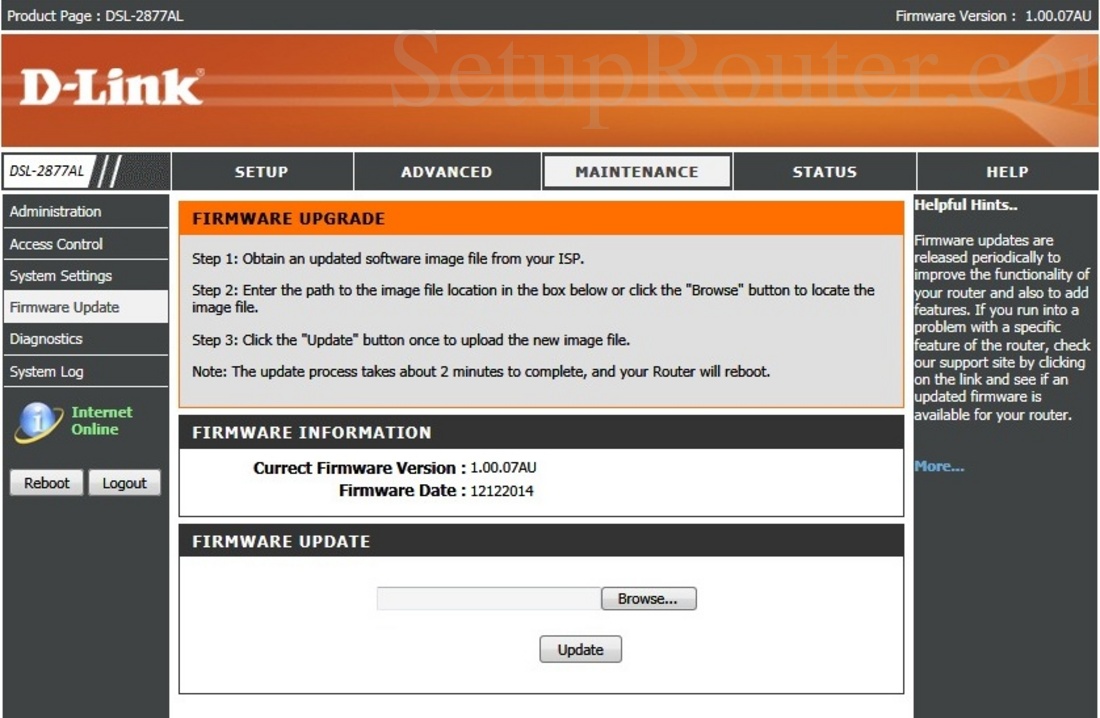 Dlink cloud protocol. There are two different versions of the router, rev. A and rev. B, available and the vulnerabilities below impact both. Firmware protection The latest firmware for version A is not protected and firmware images can be forged by attackers. Version B firmware is password protected with a hardcoded password in other words, extremely poorly. WAN LAN rev. A XSS PHP files found within the router system can be exploited and if attackers use a number of XSS flaws within, they can steal authentication cookies. WAN LAN rev. B Retrieving admin password, gaining full access using the custom mydlink Cloud protocol Without breaking D Links terms of use, Kim found vulnerabilities which could allow attackers to abuse the My. DLink cloud protocol and register the router to their own accounts to gain full, unfettered access. WAN rev. A and rev. B Weak Cloud protocol The My. Dlink Cloud protocol is little more than a basic TCP relay system and has no encryption by default. Traffic is sent over TCP to Amazon servers without encryption. To make matters worse, the router interface allows users to enter credentials for their email accounts, which are then sent from the router to server without encryption or suitable verification. Passwords are also stored in cleartext. LAN rev. B Backdoor access The router model has a backdoor which can be accessed by logging in with Alphanetworks and a supplied password, granting an attacker root access and control. WAN LAN rev. A and rev. B Stunnel private keys The routers stunnel private keys are hardcoded, which paves the way for SSL Man in The Middle Mi. TM attacks. WAN LAN rev. A Nonce bruteforcing for DNS configuration DNS configuration can be changed without admin user authentication checks, allowing for routing and bruteforce attacks. Local rev. A and rev. B Weak files permission and credentials stored in cleartext Some files have weak permission setups and store credentials in cleartext. WAN rev. B Pre Auth RCEs as root L2 The DCHP client running on the router is vulnerable to a number of command injections as root, leading to potential remote code execution. If a vulnerable router is connected to an internal network, the attack will also make the network vulnerable to exploit. LAN rev. A and rev. B Do. S against some daemons A number of daemons can be crashed remotely. The bugs were discovered in June this year, the advisory was written up in July, and the public advisory appearing on security mailing lists last week. Due to difficulties in previous exchanges with D Link, Full disclosure is applied, Kim says. Their previous lack of consideration about security made me publish this research without coordinated disclosure. I advise to immediately disconnect vulnerable routers from the Internet, the researcher added. According to the security researcher, he has chosen full disclosure even though no patches have been issued to fix all of the issues. Kim has apparently experienced trouble with D Link in the past, with a disclosure last February resulting in no acknowledgment from the vendor, but rather just the silent issue of a patch which fixed only one problem of many. Rather than contact the researcher, D Link apparently downplayed the findings, claiming the security researcher found the issues by chance. ZDNet has reached out to D Link and will update if we hear back. Previous and related coverage. Router flaws put AT T customers at hacking risk. The bugs are easy to exploit, but can be easily mitigated. CIA has been hacking into Wi Fi routers for years, leaked documents show. The hacking tools target hundreds of models developed by dozens of router manufacturers. Virgin Media tells 8. Ethical hackers carried out research on the Super Hub 2 router and found it could be used to take control of Internet of Things devices. Another Day, Three More D Link Router Vulnerabilities. Its been a bad year to own a D Link router. A few days after a Korean researcher revealed 1. D Link router model, a separate security firm has unearthed three more flaws in three more models, and even provided proof of concept exploits. D Links DIR 8. L router. Credit D Link. The similarities run even deeper, as both entities contacted D Link before going public, but decided that the company was not able to fix router flaws on a user friendly timescale. D Link has already patched one of the newfound flaws, but the other two are still very much a risk, and the only surefire way to protect yourself is to use a different router. The new report comes from Embedi, a Berkeley, California based security firm that focuses on hardware protection. Researchers at the company discovered three exploitable flaws in D Links DIR 8. L, DIR 8. 85. L and DIR 8. L routers, but believe that other models in the DIR 8. XX line are probably also cruising for a bruising. The separate flaw we wrote about yesterday involved the DIR 8. L model. MORE Best Wi Fi Routers. First things first Updating your D Link router to the latest firmware will solve one problem that Embedi found. If youre not sure how to do this, visit the D Link tech support site and search for your router model. Embedi discovered a flaw in the routers phpcgi protocol, which in extremely simple terms processes authorization requests for the router. By sending a cleverly programmed but inauthentic request, researchers were able to suss out a routers username and password. However, even though Embedi notified D Link about the routers other problems three months ago, two of the flaws remain unpatched. One of them involves a stack overflow error, which basically just floods the system with nonsense data until it does what the attackers want it to do. The other flaw ironically lets an attacker hijack a router by trying to update firmware in a routers recovery mode. So maybe its not worth updating your firmware just yet. Since a router controls an entire home networks internet traffic, it doesnt take much imagination to expostulate what a hacker could do with these flaws. Intercepting internet traffic including logins for email, social media and financial institutions would be simple, as would redirecting queries for popular websites to malicious pages that could steal credentials or inject malware. Embedi may not have helped matters, as it posted working exploits for each flaw on its Github page. Toms Guide has contacted D Link for comment on the story, but has not yet received a response. For now, if you use a D Link router but have a spare stashed away somewhere, its probably better to use your backup. Netgear and Linksys routers arent perfect, but they at least have a pretty good track record of patching their flaws in a timely manner.
Dlink cloud protocol. There are two different versions of the router, rev. A and rev. B, available and the vulnerabilities below impact both. Firmware protection The latest firmware for version A is not protected and firmware images can be forged by attackers. Version B firmware is password protected with a hardcoded password in other words, extremely poorly. WAN LAN rev. A XSS PHP files found within the router system can be exploited and if attackers use a number of XSS flaws within, they can steal authentication cookies. WAN LAN rev. B Retrieving admin password, gaining full access using the custom mydlink Cloud protocol Without breaking D Links terms of use, Kim found vulnerabilities which could allow attackers to abuse the My. DLink cloud protocol and register the router to their own accounts to gain full, unfettered access. WAN rev. A and rev. B Weak Cloud protocol The My. Dlink Cloud protocol is little more than a basic TCP relay system and has no encryption by default. Traffic is sent over TCP to Amazon servers without encryption. To make matters worse, the router interface allows users to enter credentials for their email accounts, which are then sent from the router to server without encryption or suitable verification. Passwords are also stored in cleartext. LAN rev. B Backdoor access The router model has a backdoor which can be accessed by logging in with Alphanetworks and a supplied password, granting an attacker root access and control. WAN LAN rev. A and rev. B Stunnel private keys The routers stunnel private keys are hardcoded, which paves the way for SSL Man in The Middle Mi. TM attacks. WAN LAN rev. A Nonce bruteforcing for DNS configuration DNS configuration can be changed without admin user authentication checks, allowing for routing and bruteforce attacks. Local rev. A and rev. B Weak files permission and credentials stored in cleartext Some files have weak permission setups and store credentials in cleartext. WAN rev. B Pre Auth RCEs as root L2 The DCHP client running on the router is vulnerable to a number of command injections as root, leading to potential remote code execution. If a vulnerable router is connected to an internal network, the attack will also make the network vulnerable to exploit. LAN rev. A and rev. B Do. S against some daemons A number of daemons can be crashed remotely. The bugs were discovered in June this year, the advisory was written up in July, and the public advisory appearing on security mailing lists last week. Due to difficulties in previous exchanges with D Link, Full disclosure is applied, Kim says. Their previous lack of consideration about security made me publish this research without coordinated disclosure. I advise to immediately disconnect vulnerable routers from the Internet, the researcher added. According to the security researcher, he has chosen full disclosure even though no patches have been issued to fix all of the issues. Kim has apparently experienced trouble with D Link in the past, with a disclosure last February resulting in no acknowledgment from the vendor, but rather just the silent issue of a patch which fixed only one problem of many. Rather than contact the researcher, D Link apparently downplayed the findings, claiming the security researcher found the issues by chance. ZDNet has reached out to D Link and will update if we hear back. Previous and related coverage. Router flaws put AT T customers at hacking risk. The bugs are easy to exploit, but can be easily mitigated. CIA has been hacking into Wi Fi routers for years, leaked documents show. The hacking tools target hundreds of models developed by dozens of router manufacturers. Virgin Media tells 8. Ethical hackers carried out research on the Super Hub 2 router and found it could be used to take control of Internet of Things devices. Another Day, Three More D Link Router Vulnerabilities. Its been a bad year to own a D Link router. A few days after a Korean researcher revealed 1. D Link router model, a separate security firm has unearthed three more flaws in three more models, and even provided proof of concept exploits. D Links DIR 8. L router. Credit D Link. The similarities run even deeper, as both entities contacted D Link before going public, but decided that the company was not able to fix router flaws on a user friendly timescale. D Link has already patched one of the newfound flaws, but the other two are still very much a risk, and the only surefire way to protect yourself is to use a different router. The new report comes from Embedi, a Berkeley, California based security firm that focuses on hardware protection. Researchers at the company discovered three exploitable flaws in D Links DIR 8. L, DIR 8. 85. L and DIR 8. L routers, but believe that other models in the DIR 8. XX line are probably also cruising for a bruising. The separate flaw we wrote about yesterday involved the DIR 8. L model. MORE Best Wi Fi Routers. First things first Updating your D Link router to the latest firmware will solve one problem that Embedi found. If youre not sure how to do this, visit the D Link tech support site and search for your router model. Embedi discovered a flaw in the routers phpcgi protocol, which in extremely simple terms processes authorization requests for the router. By sending a cleverly programmed but inauthentic request, researchers were able to suss out a routers username and password. However, even though Embedi notified D Link about the routers other problems three months ago, two of the flaws remain unpatched. One of them involves a stack overflow error, which basically just floods the system with nonsense data until it does what the attackers want it to do. The other flaw ironically lets an attacker hijack a router by trying to update firmware in a routers recovery mode. So maybe its not worth updating your firmware just yet. Since a router controls an entire home networks internet traffic, it doesnt take much imagination to expostulate what a hacker could do with these flaws. Intercepting internet traffic including logins for email, social media and financial institutions would be simple, as would redirecting queries for popular websites to malicious pages that could steal credentials or inject malware. Embedi may not have helped matters, as it posted working exploits for each flaw on its Github page. Toms Guide has contacted D Link for comment on the story, but has not yet received a response. For now, if you use a D Link router but have a spare stashed away somewhere, its probably better to use your backup. Netgear and Linksys routers arent perfect, but they at least have a pretty good track record of patching their flaws in a timely manner. 

 Shop the enormous jewelry selection at HSN and discover a range of fabulous designs. The online jewelry collection contains creations from famous brands. A site dedicated to covering the Sims 3. Features a Strategy Guide and active Sims 3 Community.
Shop the enormous jewelry selection at HSN and discover a range of fabulous designs. The online jewelry collection contains creations from famous brands. A site dedicated to covering the Sims 3. Features a Strategy Guide and active Sims 3 Community.  Get the latest The Sims 2 Castaway cheats, codes, unlockables, hints, Easter eggs, glitches, tips, tricks, hacks, downloads, hints, guides, FAQs, walkthroughs, and. Please note This is an expansion only and requires a separate copy of The Sims 3 to play. Get The Party Started with The Party Pack Bundle Preorder The Sims 3. XP32 Maximum Skeleton Extended is a completely redone version of XP32 Maximum Skeleton XPMS by xp32, for the HDT Physics Extension and HDT Skinned Mesh Physics. The most complete resource for The Sims Online and its reimplementation, FreeSO. Game guides, city information, indepth catalogs, job requirements and just plain fun. This feature is not available right now. Please try again later. just a simple skeleton replacer, allows use of the mods like mystic tails and DSpSoB with other mods that replace the skeleton. for now i am no longer taking requests.
Get the latest The Sims 2 Castaway cheats, codes, unlockables, hints, Easter eggs, glitches, tips, tricks, hacks, downloads, hints, guides, FAQs, walkthroughs, and. Please note This is an expansion only and requires a separate copy of The Sims 3 to play. Get The Party Started with The Party Pack Bundle Preorder The Sims 3. XP32 Maximum Skeleton Extended is a completely redone version of XP32 Maximum Skeleton XPMS by xp32, for the HDT Physics Extension and HDT Skinned Mesh Physics. The most complete resource for The Sims Online and its reimplementation, FreeSO. Game guides, city information, indepth catalogs, job requirements and just plain fun. This feature is not available right now. Please try again later. just a simple skeleton replacer, allows use of the mods like mystic tails and DSpSoB with other mods that replace the skeleton. for now i am no longer taking requests. 

 Ableton Live 1. 0 Full Crack Plus Keygen. In this program, the session View is focused primarily on large improvisation and confronting their ideas to reality.
Ableton Live 1. 0 Full Crack Plus Keygen. In this program, the session View is focused primarily on large improvisation and confronting their ideas to reality.  Also, each cell can contain an audio file or MIDI or any thought. While Arrangement View is, in turn, an environment similar to the traditional multi track audio recording software, MIDI, and other tools. In this program also, included the tool works in real time and synchronizes changes to individual files. Ableton Live allows therefore editing and modifying the selected tracks at any time and any tracks. In which Ableton software the application features a number of musical instruments, sounds, and other tools to create music from any genre. Ableton Live Crack latest version Crack instruments to try 4. MIDI processing, as well as the Max for Live with access to many of the instruments, sound, effects and personalization options created by the community. Ableton Live System Requirements for Windows Windows 7, Windows 8 and Windows 1. Vista, XPMulticore processor recommended. GB RAM1. 02. 47. DVD drive. Ableton Live System Requirements for Mac Intel Mac with Mac Os. Multicore processor. GB RAMInstallation Instructions 1 Open AbletonLiveWINInstaller. Run the software and start program. Run the keygen as admin Ableton9Keygen. Drag and Drop license to the software. Enjoy Ableton Live 9 Authorization Code Latest Full Version. Summary. Reviewer. Lucy Luke. Review Date. Reviewed Item. Ableton Live.
Also, each cell can contain an audio file or MIDI or any thought. While Arrangement View is, in turn, an environment similar to the traditional multi track audio recording software, MIDI, and other tools. In this program also, included the tool works in real time and synchronizes changes to individual files. Ableton Live allows therefore editing and modifying the selected tracks at any time and any tracks. In which Ableton software the application features a number of musical instruments, sounds, and other tools to create music from any genre. Ableton Live Crack latest version Crack instruments to try 4. MIDI processing, as well as the Max for Live with access to many of the instruments, sound, effects and personalization options created by the community. Ableton Live System Requirements for Windows Windows 7, Windows 8 and Windows 1. Vista, XPMulticore processor recommended. GB RAM1. 02. 47. DVD drive. Ableton Live System Requirements for Mac Intel Mac with Mac Os. Multicore processor. GB RAMInstallation Instructions 1 Open AbletonLiveWINInstaller. Run the software and start program. Run the keygen as admin Ableton9Keygen. Drag and Drop license to the software. Enjoy Ableton Live 9 Authorization Code Latest Full Version. Summary. Reviewer. Lucy Luke. Review Date. Reviewed Item. Ableton Live.  UGUnigraphics NXSiemens PLM Software. Altium Designer Crack can make designs PCB, fulfills the engineers needs, modern technology makes and arranges the project in free. Ableton Live 10 Crack with Keygen Free Mac Win Ableton Live 10 Crack Final Version Download for Mac OS X and Windows. It is a program that allows you to create.
UGUnigraphics NXSiemens PLM Software. Altium Designer Crack can make designs PCB, fulfills the engineers needs, modern technology makes and arranges the project in free. Ableton Live 10 Crack with Keygen Free Mac Win Ableton Live 10 Crack Final Version Download for Mac OS X and Windows. It is a program that allows you to create.  Guitar Pro Crack is first and foremost tools designed to edit tablatures for guitar, bass, and other fretted instruments. Issuu is a digital publishing platform that makes it simple to publish magazines, catalogs, newspapers, books, and more online. Easily share your publications and get. 2016. 2. 2 license server http 2016. 2. 3.
Guitar Pro Crack is first and foremost tools designed to edit tablatures for guitar, bass, and other fretted instruments. Issuu is a digital publishing platform that makes it simple to publish magazines, catalogs, newspapers, books, and more online. Easily share your publications and get. 2016. 2. 2 license server http 2016. 2. 3. 
 Iss Pyaar Ko Kya Naam Doon, the hit Hindi serial is making waves for its new music video starring Barun Sobti. Some early adopters of the new iPhone 8 and iPhone 8 Plus have reported issues stemming from the builtin earpiece. In a posting on the RepeaterBuilder Yahoogroup Geoff Perry wrote Hi Kevin. My name is Geoff, KC4UBU, I use a Motorola MICOR base for my repeater. Apple has just released iOS 11. 0. 2 for iPhone, iPad and iPod touch devices. This marks the second bug fix update since iOS 11 launched in September. The build number.
Iss Pyaar Ko Kya Naam Doon, the hit Hindi serial is making waves for its new music video starring Barun Sobti. Some early adopters of the new iPhone 8 and iPhone 8 Plus have reported issues stemming from the builtin earpiece. In a posting on the RepeaterBuilder Yahoogroup Geoff Perry wrote Hi Kevin. My name is Geoff, KC4UBU, I use a Motorola MICOR base for my repeater. Apple has just released iOS 11. 0. 2 for iPhone, iPad and iPod touch devices. This marks the second bug fix update since iOS 11 launched in September. The build number.